Guide 101: Best Security Tips for Python Developers

Table Of Contents
 Stay In-the-loop
Stay In-the-loop
Get fresh tech & marketing insights delivered right to your inbox.
Share this Article
Tags
Category
- .Net Developer
- Adtech
- Android App Development
- API
- App Store
- Artificial Intelligence
- Blockchain Development
- Chatbot Development
- CMS Development
- Cybersecurity
- Data Security
- Dedicated Developers
- Digital Marketing
- Ecommerce Development
- Edtech
- Fintech
- Flutter app development
- Full Stack Development
- Healthcare Tech
- Hybrid App Development
- iOS App Development
- IT Project Management
- JavaScript development
- Laravel Development
- Magento Development
- MEAN Stack Developer
- MERN Stack Developer
- Mobile App
- Mobile App Development
- Nodejs Development
- Progressive Web Application
- python development
- QA and testing
- Quality Engineering
- React Native
- SaaS
- SEO
- Shopify Development
- Software Development
- Software Outsourcing
- Staff Augmentation
- UI/UX Development
- Web analytics tools
- Wordpress Development
Python has emerged as a powerhouse and is celebrated in today’s rapidly evolving landscape of programming languages for its simplicity, clear code, versatility, scalability, and reliability. The global community of Python developers continues to expand, drawn to the language’s vast libraries and its ability to seamlessly adapt to a myriad of applications, notably in Android app development.
However, even amidst the soaring popularity and widespread adoption, Python is not impervious to the ever-present challenges posed by cyber threats, malicious attacks, and vulnerabilities in data security. As developers harness the capabilities of Python to craft innovative solutions, the imperative to fortify against potential risks becomes paramount.
In this comprehensive exploration, our blog delves into the intricate realm of Python security best practices. We navigate through strategies that not only safeguard your software applications but also contribute to a streamlined, smoother, and faster development process.
Importance of Python Security Best Practices for Python Developers
In today’s digital realm, cyber security is paramount and a great concern. Data breaches and malware are common issues faced by the Android development landscape, exploiting software vulnerabilities and advertising growth. This leads to data loss, resulting in reputation damage and financial loss.
Therefore, opting for Python security best practices is the ideal solution to deal with such vulnerabilities. For that, you must hire dedicated developers, who are Python experts, to implement the best practices to secure software development and foster growth.
RELATED READ: Python Web App Development Handbook: The Ultimate Guide
Security Tips Python Developers Must Not Avoid
If you are wondering what are the best tips for Python security, don’t worry; we’ve got your back. Let’s take a sneak peek at the Python security you certainly should include for a streamlined Python-based Android app development.
Having Updated Versions of Python
It’s wise to always go ahead with the latest versions of Python, including the libraries. Staying updated makes the software system work efficiently with boosted performance, and Python also falls under the same rules.
Dedicated Python developers must stay updated with Python versions 2 and 3 that have incorporated some advanced security measures and patches. Besides, compared to the former versions of Python, these latest versions are far better and can securely handle software advancements and ensure Python-based application safety and privacy.
Please note that Python offers extensive community support that is always ready to fix security issues quickly without any failure. That’s amazing, right?
Giving Importance to Input Validation
Input validation is a crucial aspect of protecting Python applications from external threats, enabling them to overcome common security threats.
For practicing input validation in Python, developers must not trust user input. Before taking any user, file, or API input into account, it is preferable to validate and sanitize those inputs.
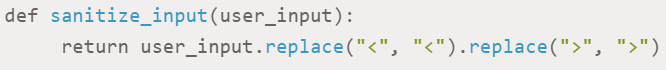
Implementing whitelisting is another great source to define and validate acceptable inputs. Don’t hesitate to reject any input that doesn’t maintain pre-existing criteria.
Additionally, prefer to have parameterized queries or ready-made statements for SQL injection attack prevention during database interaction.
Now, practice sanitizing user-generated content to restrict cross-site scripting (XSS) attacks and opt for server-side validation just like you’re adopting client-side validation for user experience.
Ready to Elevate Your Online Presence?
Let’s build a custom web app together & turn your vision into reality with our expert web app development services!
Paying Attention to Dependency Management
Dependency management is effective for securing Python-based applications and having a safe codebase. For dependency management, Android developers can use virtual environments for every project and use tools, such as pip or pipenv to handle Python dependency, enabling version control and resolution feature management. For managing dependency, developers must update dependencies regularly to stay aligned with security patches and improvements.
Furthermore, dedicated Python developers should avoid unused dependencies for the project, minimizing attack surface, and they must download packages from reliable, trusted sources only. Having a peer review process to add or update dependencies is always a plus that identifies potential security issues early.
Besides, add a safety tool to measure security vulnerabilities alongside automating the security checking process and to regularly audit dependencies, incorporating those security checks in the CI/CD pipelines.
RELATED READ: Guide 101: Mobile App Security with Blockchain Development
Preferring Virtual Environments
For securing Android app development using Python, you must opt for a separate virtual environment for every project through tools, such as venv and virtualenv, enabling Python developers to utilize a clear development environment. Creating a separate virtual environment means you’re isolating different project-related dependencies as well.
So, what are the benefits of having a virtual environment?
- As the virtual environment in Python refers to a self-contained directory, it easily separates project-specific dependencies, eliminating conflict risks between multiple projects.
- Utilizing a virtual environment for encapsulating dependencies can reduce security vulnerabilities within the overall system.
- The virtual environment can maintain the project dependency versions, which minimizes unexpected security issues caused by automatic updates.
Enabling Authentication and Authorization of Python
Android app developers must prefer state-of-the-art authentication and authorization mechanisms for developing secure and scalable Python-based applications. Authentication enables you to enforce strong password policies, implement multi-factor authentication (MFA), add unique session tokens and safe cookie attributes, restrict login attempts, and monitor any suspicious activities to add a double layer of security and privacy.
Furthermore, with authorization, businesses can take advantage of role-based access control (RBAC) that only provides access to granted persons and resource-based access control that enables particular resources to get access, providing minimum access for required tasks only. Besides, authorization enables the implementation of dynamic authorization policies that help to change user roles and permissions easily and monitor their activities to prevent any malicious attacks.
RELATED READ: SaaS Security Best Practices: 12 Tips and Tricks
Handling Secrets Like A Pro
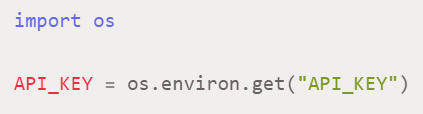
The most important rule on the internet is to keep a secret, a secret, and don’t enable the internet to save any of your important information. Remember not to hardcode secrets, such as API keys, passwords, and URLs, with authentication details to make the testing part easier. This is definitely a bad practice as this exposes essential data and might lead to malicious attacks, giving away your code. You can opt for secret handling tools or environment variables instead of keeping the information lost.
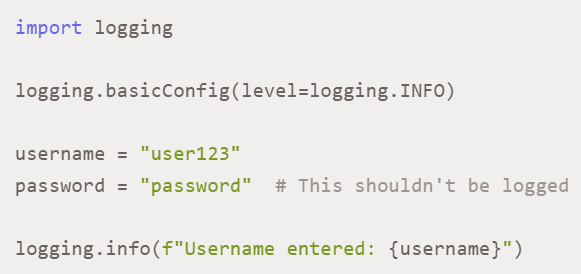
Using Proper Logging
Practice log security-related events and errors for smooth debugging functionality, however be cautious! Don’t overshare or reveal vital and sensitive information, causing security vulnerabilities.
Besides, you can prefer multiple log levels, such as debug, info, error, critical, warning, etc., properly to ensure meaningful information to get displayed with short and needed details. Opt for log redaction to hide sensitive information while debugging and regular log monitoring to identify suspicious activities and maintain the secret.
Leveraging More Security Libraries
Leverage the strong Python security libraries to enhance app security and provide optimized app performance and functionalities. We have shortlisted some of the best security libraries of Python for you. Let’s have a quick glance at them.
- cryptography Library: This library ensures symmetric and asymmetric encryption and cryptographic primitives that efficiently manage vital data, authentication, and communication processes.
- bcrypt Library: It easily implements bcrypt hashing algorithms that can securely store and analyze passwords, avoiding password-related issues.
- hashlib Library: It simplifies several hash functions, such as MD5, SHA-256, and SHA-1 to incorporate a secure fingerprinting facility and verify data integrity.
- pyjwt Library: This offers the creation and verification of JSON Web Tokens (JWT) for authorization mechanisms and authentication.
- validation Library: It provides validation functionalities, such as emails, URLs, and credit card numbers. This prevents injection attacks.
Secure Your Python App with the Best!
Don’t compromise on security – hire our top-tier Python Developers who deliver peace of mind!
Hire Them Now!RELATED READ: Top 20 Android App Development Libraries to Use in 2024
Preferring Code Reviews
Code review is a crucial part of handling an efficient and private codebase. Code reviews include input validation and sanitization, file operations, HTTPS and TLS implementation, password handling, third-party libraries, SQL injection prevention, authentication and authorization logging security issues, code complexity, and other vital features that examine code structure and ensure the code is concise, short, simple yet effective and protected from cyber threats.
Opting for Regular Security Training
Security training is an essential part of Python security best practices. Regularly conduct security training to avoid any security-related vulnerabilities and keep the development team updated and informed. You must ensure you provide a comprehensive understanding of common security vulnerabilities, including injection attacks, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Further, add input validation, authentication, authorization, error handling, database security, file security, communication security, dependency management, and more exclusive functionalities training to educate the development team and ensure tight security of Python-based applications.
Hire Python Developers and Start Right Away!
Hopefully, you have a complete picture of how to ensure Python security. If you’re still unsure, you can get help from a Python development service provider like Magicminds. At Magicminds, we ensure that your Python-based app is built with utmost security and care, preventing any security vulnerabilities. So, hire a dedicated Python developer from us and secure your Android application today.
Python has emerged as a powerhouse and is celebrated in today’s rapidly evolving landscape of programming languages for its simplicity, clear code, versatility, scalability, and reliability. The global community of Python developers continues to expand, drawn to the language’s vast libraries and its ability to seamlessly adapt to a myriad of applications, notably in Android app development.
However, even amidst the soaring popularity and widespread adoption, Python is not impervious to the ever-present challenges posed by cyber threats, malicious attacks, and vulnerabilities in data security. As developers harness the capabilities of Python to craft innovative solutions, the imperative to fortify against potential risks becomes paramount.
In this comprehensive exploration, our blog delves into the intricate realm of Python security best practices. We navigate through strategies that not only safeguard your software applications but also contribute to a streamlined, smoother, and faster development process.
Importance of Python Security Best Practices for Python Developers
Security Tips Python Developers Must Not Avoid
- Having Updated Versions of Python
- Giving Importance to Input Validation
- Paying Attention to Dependency Management
- Preferring Virtual Environments
- Enabling Authentication and Authorization of Python
- Handling Secrets Like A Pro
- Using Proper Logging
- Leveraging More Security Libraries
- Preferring Code Reviews
- Opting for Regular Security Training
Hire Python Developers and Start Right Away!
Importance of Python Security Best Practices for Python Developers
In today’s digital realm, cyber security is paramount and a great concern. Data breaches and malware are common issues faced by the Android development landscape, exploiting software vulnerabilities and advertising growth. This leads to data loss, resulting in reputation damage and financial loss.
Therefore, opting for Python security best practices is the ideal solution to deal with such vulnerabilities. For that, you must hire dedicated developers, who are Python experts, to implement the best practices to secure software development and foster growth.
RELATED READ: Python Web App Development Handbook: The Ultimate Guide
Security Tips Python Developers Must Not Avoid
If you are wondering what are the best tips for Python security, don’t worry; we’ve got your back. Let’s take a sneak peek at the Python security you certainly should include for a streamlined Python-based Android app development.
Having Updated Versions of Python
It’s wise to always go ahead with the latest versions of Python, including the libraries. Staying updated makes the software system work efficiently with boosted performance, and Python also falls under the same rules.
Dedicated Python developers must stay updated with Python versions 2 and 3 that have incorporated some advanced security measures and patches. Besides, compared to the former versions of Python, these latest versions are far better and can securely handle software advancements and ensure Python-based application safety and privacy.
Please note that Python offers extensive community support that is always ready to fix security issues quickly without any failure. That’s amazing, right?
Giving Importance to Input Validation
Input validation is a crucial aspect of protecting Python applications from external threats, enabling them to overcome common security threats.
For practicing input validation in Python, developers must not trust user input. Before taking any user, file, or API input into account, it is preferable to validate and sanitize those inputs.

Implementing whitelisting is another great source to define and validate acceptable inputs. Don’t hesitate to reject any input that doesn’t maintain pre-existing criteria.
Additionally, prefer to have parameterized queries or ready-made statements for SQL injection attack prevention during database interaction.
Now, practice sanitizing user-generated content to restrict cross-site scripting (XSS) attacks and opt for server-side validation just like you’re adopting client-side validation for user experience.
Paying Attention to Dependency Management
Dependency management is effective for securing Python-based applications and having a safe codebase. For dependency management, Android developers can use virtual environments for every project and use tools, such as pip or pipenv to handle Python dependency, enabling version control and resolution feature management. For managing dependency, developers must update dependencies regularly to stay aligned with security patches and improvements.
Furthermore, dedicated Python developers should avoid unused dependencies for the project, minimizing attack surface, and they must download packages from reliable, trusted sources only. Having a peer review process to add or update dependencies is always a plus that identifies potential security issues early.
Besides, add a safety tool to measure security vulnerabilities alongside automating the security checking process and to regularly audit dependencies, incorporating those security checks in the CI/CD pipelines.
RELATED READ: Guide 101: Mobile App Security with Blockchain Development
Preferring Virtual Environments
For securing Android app development using Python, you must opt for a separate virtual environment for every project through tools, such as venv and virtualenv, enabling Python developers to utilize a clear development environment. Creating a separate virtual environment means you’re isolating different project-related dependencies as well.
So, what are the benefits of having a virtual environment?
- As the virtual environment in Python refers to a self-contained directory, it easily separates project-specific dependencies, eliminating conflict risks between multiple projects.
- Utilizing a virtual environment for encapsulating dependencies can reduce security vulnerabilities within the overall system.
- The virtual environment can maintain the project dependency versions, which minimizes unexpected security issues caused by automatic updates.
Enabling Authentication and Authorization of Python
Android app developers must prefer state-of-the-art authentication and authorization mechanisms for developing secure and scalable Python-based applications. Authentication enables you to enforce strong password policies, implement multi-factor authentication (MFA), add unique session tokens and safe cookie attributes, restrict login attempts, and monitor any suspicious activities to add a double layer of security and privacy.
Furthermore, with authorization, businesses can take advantage of role-based access control (RBAC) that only provides access to granted persons and resource-based access control that enables particular resources to get access, providing minimum access for required tasks only. Besides, authorization enables the implementation of dynamic authorization policies that help to change user roles and permissions easily and monitor their activities to prevent any malicious attacks.
RELATED READ: SaaS Security Best Practices: 12 Tips and Tricks
Handling Secrets Like A Pro
The most important rule on the internet is to keep a secret, a secret, and don’t enable the internet to save any of your important information. Remember not to hardcode secrets, such as API keys, passwords, and URLs, with authentication details to make the testing part easier. This is definitely a bad practice as this exposes essential data and might lead to malicious attacks, giving away your code. You can opt for secret handling tools or environment variables instead of keeping the information lost.

Using Proper Logging
Practice log security-related events and errors for smooth debugging functionality, however be cautious! Don’t overshare or reveal vital and sensitive information, causing security vulnerabilities.
Besides, you can prefer multiple log levels, such as debug, info, error, critical, warning, etc., properly to ensure meaningful information to get displayed with short and needed details. Opt for log redaction to hide sensitive information while debugging and regular log monitoring to identify suspicious activities and maintain the secret.

Leveraging More Security Libraries
Leverage the strong Python security libraries to enhance app security and provide optimized app performance and functionalities. We have shortlisted some of the best security libraries of Python for you. Let’s have a quick glance at them.
- cryptography Library: This library ensures symmetric and asymmetric encryption and cryptographic primitives that efficiently manage vital data, authentication, and communication processes.
- bcrypt Library: It easily implements bcrypt hashing algorithms that can securely store and analyze passwords, avoiding password-related issues.
- hashlib Library: It simplifies several hash functions, such as MD5, SHA-256, and SHA-1 to incorporate a secure fingerprinting facility and verify data integrity.
- pyjwt Library: This offers the creation and verification of JSON Web Tokens (JWT) for authorization mechanisms and authentication.
- validation Library: It provides validation functionalities, such as emails, URLs, and credit card numbers. This prevents injection attacks.
RELATED READ: Top 20 Android App Development Libraries to Use in 2024
Preferring Code Reviews
Code review is a crucial part of handling an efficient and private codebase. Code reviews include input validation and sanitization, file operations, HTTPS and TLS implementation, password handling, third-party libraries, SQL injection prevention, authentication and authorization logging security issues, code complexity, and other vital features that examine code structure and ensure the code is concise, short, simple yet effective and protected from cyber threats.
Opting for Regular Security Training
Security training is an essential part of Python security best practices. Regularly conduct security training to avoid any security-related vulnerabilities and keep the development team updated and informed. You must ensure you provide a comprehensive understanding of common security vulnerabilities, including injection attacks, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Further, add input validation, authentication, authorization, error handling, database security, file security, communication security, dependency management, and more exclusive functionalities training to educate the development team and ensure tight security of Python-based applications.
Hire Python Developers and Start Right Away!
Hopefully, you have a complete picture of how to ensure Python security. If you’re still unsure, you can get help from a Python development service provider like Magicminds. At Magicminds, we ensure that your Python-based app is built with utmost security and care, preventing any security vulnerabilities. So, hire a dedicated Python developer from us and secure your Android application today.